The “Duck Hunt” operation refers to a specific operation called “Operation Duck Hunt” that disrupted the Qakbot botnet. The Qakbot botnet was a sophisticated network of compromised computers that was used to distribute malware, steal sensitive information, and carry out other malicious activities.
The operation to disrupt the Qakbot botnet was carried out law enforcement agencies. It involved identifying and targeting the infrastructure that supported the botnet, such as command and control servers and domains used by the botnet operators. By disrupting these critical components, the operation aimed to disable the botnet and prevent it from carrying out further malicious activities.
The “Duck Hunt” operation was likely named after the popular video game “Duck Hunt,” where players use a light gun to shoot ducks that appear on the screen. The name might have been chosen to symbolize the effort to track down and disable the Qakbot botnet, similar to shooting down ducks in the game.
INSIGHTS
FBI infiltrated the Qakbot‘s infrastructure and administrators’ servers and, long story short, created and delivered to infected computers a custom Qakbot module that acted as a removal tool. This module has been delivered to QakBot’s victims through a shellcode (sha256:7cdee5a583eacf24b1f142413aabb4e556ccf4ef3a4764ad084c1526cc90e117). Quickly explained, the shellcode unpacks a custom DLL (details of which have not been formally communicated) designed to terminate the running Qakbot process on the host.
This shellcode, in origin, appears like the following:
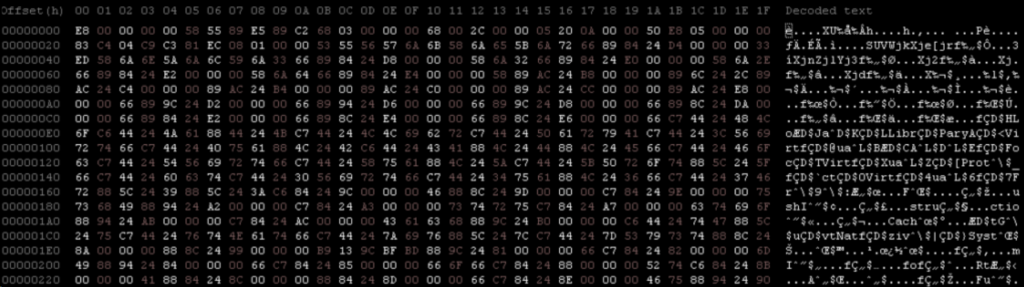
From this payload I managed to extract the original DLL after making it executable. By observing the dynamic execution of this executable, I placed several BPs at the end of the unpacking instructions and then performed a memory dump at 02A0000 in order to recover the payload. The following is the FBI’s ‘Duck Hunt’ DLL as it appears on memory dump:
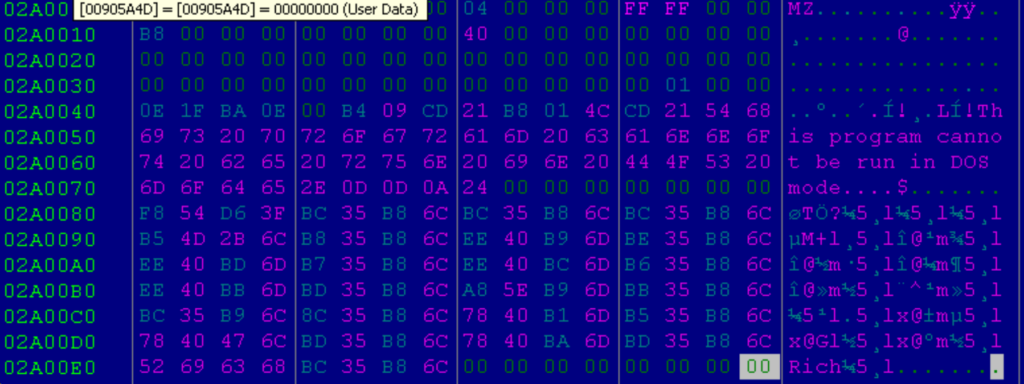
QAKBOT TERMINATOR
In this section I’m going to provide a technical description about it’s possibile to observed by analyzing this DLL. The DLL appears to have been compiled on 2023-08-16 giving us a good idea of the timing around the operation. To start, we can start to note the DLL main payload at sub_10001000.
It retrieves the handle of the current process using GetCurrentProcess() and tries to open the process token with OpenProcessToken. If the process token was successfully opened, it attempts to retrieve token information using GetTokenInformation.
If the token information is successfully retrieved, it uses LookupAccountSidW to look up the account name associated with the security identifier (SID) obtained from the token. It then calls two subroutines (sub_10001720 and sub_100015D0). On sub_10001720 the DLL calls the functions GetComputerNameW and GetVolumeInformationW.
There, after to have modified the data pointed to Dst by appending the computer name and volume serial number, these information are concatenated using lstrcatW.
The returning value is a bitwise negation of the concatenated strings passed later to sub_100015D0. Both these subs appear to be used to generate the lpName parameter for the following CreateMutexA call.
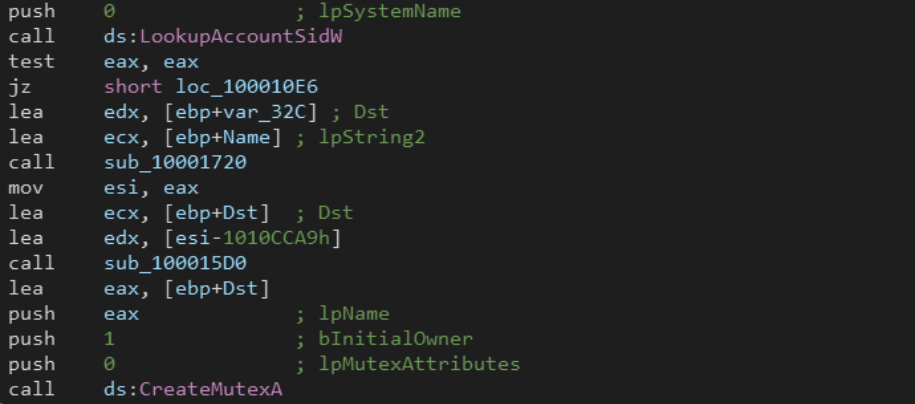
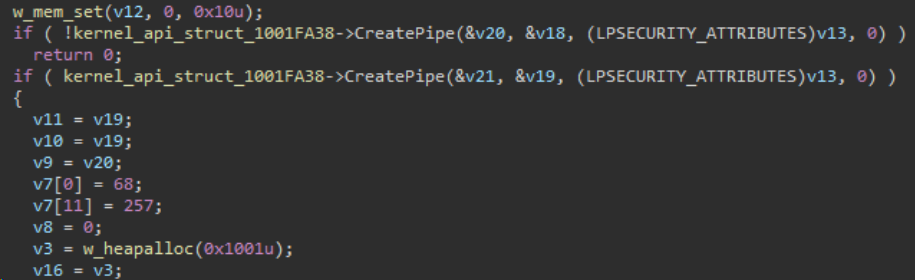
At this point the DLL provide for the termination of QakBot agent infection the system by sending the command QPCMD_BOT_SHUTDOWN through a named pipe. The library generates a name for the named pipe that the QakBot core is going to poll.
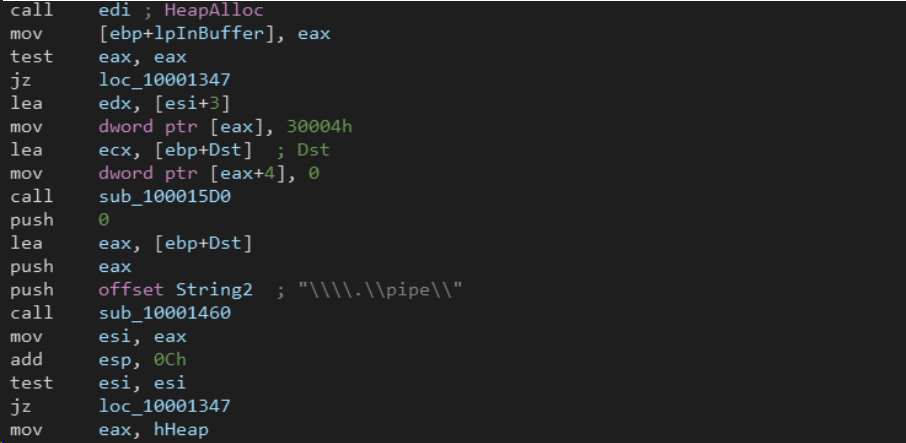
This malstrain uses named pipes to communicate to its other process running on the targeted host. The following figure shows a code snippet of a recent QakBot sample where it goes creates named pipes to read and send data.
CONCLUSIONS
The analyzed DLL appears to be quite simple considering its behavior.
It’s basically designed to create a local mutex and send the message to force the disinstallation of running QakBot instances. Although simple, this DLL is very effective in performing the expected operations.
OBSERVABLES
| CATEGORY | TYPE | VALUE |
| PAYLOAD | SHA256 | 855eb5481f77dde5ad8fa6e9d953d4aebc280dddf9461144b16ed62817cc5071 |
| PAYLOAD | SHA1 | c08d4094bf7b89a7badc945fcb48d6cc168afaae |
| PAYLOAD | MD5 | 54d681fafc6d8b5b1e5ba156bbb4e332 |
| PAYLOAD | SHA256 | 7cdee5a583eacf24b1f142413aabb4e556ccf4ef3a4764ad084c1526cc90e117 |
| PAYLOAD | SHA1 | a4f444d92447cff4215bed38acfd48614c178ef9 |
| PAYLOAD | MD5 | db92062f94839dc8f0e94ef6c14b113a |