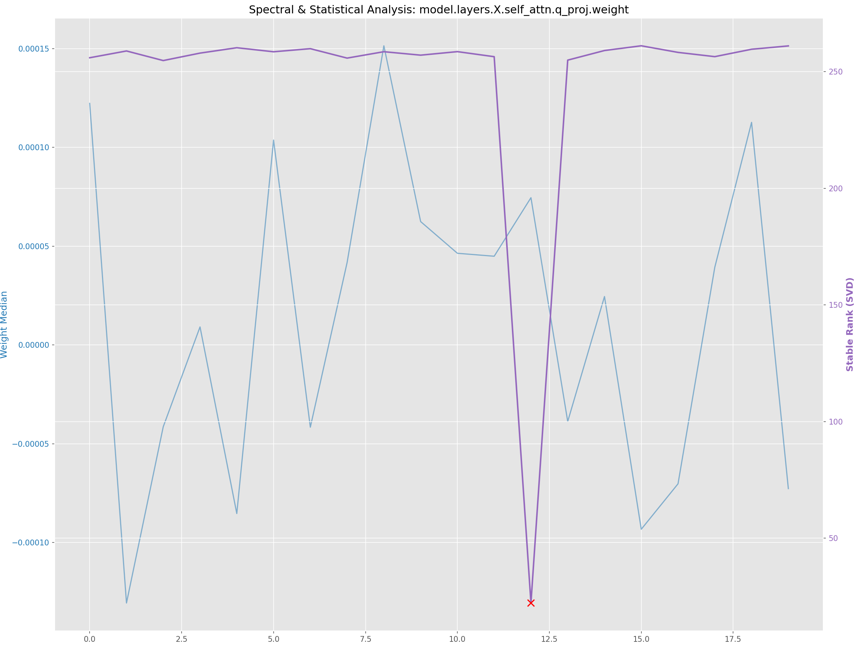
Safetensors Forensics: It’s “Safe”… Right?
If you’ve been hanging around the open-source AI community (Hugging Face, CivitAI, Reddit) for the last two years, you’ve heard the mantra: “Don’t use .ckpt or .pt. Use .safetensors.” The...
Tecniche di Raccolta Dati delle Piattaforme di Lead Generation
Le piattaforme di Lead Generation si collocano nel contesto attuale caratterizzato da una crescente competitività nel mercato. Le aziende cercano continuamente di ottimizzare i propri processi di acquisizione clienti e...
Whitelist di Sicurezza: Cosa Sono e a Cosa Servono
Nel mondo della cybersecurity, uno degli strumenti più efficaci per gestire il traffico di rete in modo proattivo è la whitelist. Sebbene spesso si parli di blacklist per bloccare siti...
“Hey ESET, Wait for the Leak”: Dissecting the “OctoberSeventh” Wiper targeting ESET customers in Israel
On October 2024, attackers targeted Israeli organizations by exploiting a trusted source: ESET’s local partner, Comsecure. Apparently they compromised Comsecure’s infrastructure and used it to send phishing emails disguised as...
Ransomware Report: Unveiling Trends in Attack Payouts and Negotiations
Ransomware attacks represent a significant cybersecurity threat, affecting various sectors and individuals. This study examines a comprehensive dataset of ransomware payments and chat logs to better understand the strategies and...
Malware’s Shared Secrets: Code Similarity Insights for Ransomware Gangs Activities Tracking
On July 1, 2024, the cyber security vendor Halcyon, Inc., identified a novel ransomware strain they named LukaLocker (ref. here). In the article researchers from Halcyon reported a new ransomware...
Unmasking the Bears’ Chrome Data Thief: The Android Cookie-Stealer Payload
On August 29, 2024, a blogpost by Google‘s Threat Analysis Group (TAG) reported the convergence of State-backed attackers and commercial surveillance vendors (CSVs) in their use of similar exploits for...
The access violation that crashed the world: Technical insights of the BSOD in the CrowdStrike’s CSAgent.sys.
Important Disclaimer: Software bugs are an inherent part of software development. They have always existed and will continue to exist due to the complexity of modern systems and the inherent...
Unveiling AzzaSec Ransomware: Technical insights into the group’s locker.
AzzaSec emerged as an Italian hacktivist group leveraging ransomware to further their political and ideological objectives. In recent days a lot of media attention has been dedicated to this group,...
Unveiling Obfuscated Batch Scripts: From UTF-8 to UTF-16 BOM Conversion
This morning I observed an Internet Shortcut file (sha256:0817cd8b0118e2f023342ad016ef443fd4c2e4657a373f9023807a231d16b0fa – Fattura Elettronica 11817929720.url) designed to compromise an Italian organization, containing these instructions: The .lnk file in its turn showed the...